Alabama-based Intergraph (now part of Stockholm-based Hexagon) is a global leader in providing information technology for industrial and geospatial applications to create autonomous connected systems. With over 20,000 employees across the globe, they are a major provider of asset life cycle solutions for the design, construction, and operation of hyperscale industrial facilities such as nuclear submarines and plants.
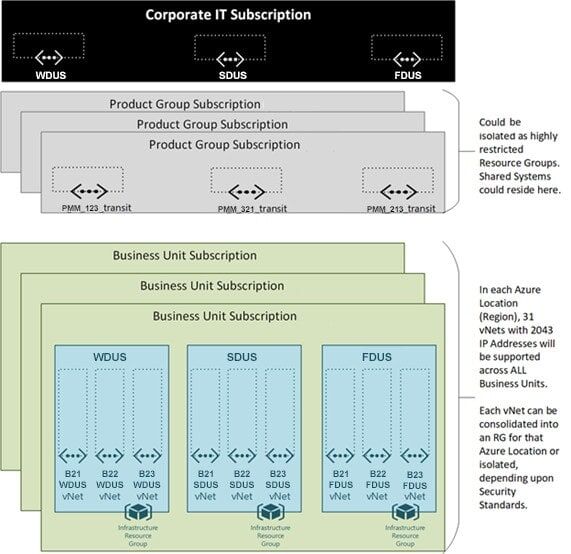
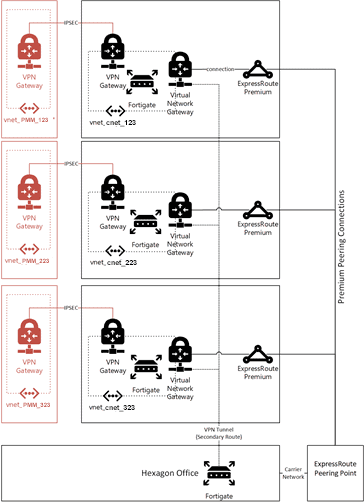
Intergraph engaged Atmosera to assist in envisioning and implementing an Azure Network Infrastructure that would scale to support the unique needs of Intergraph while minimizing Network Administration and Management.