At a recent SecureWorld conference, Atmosera’s Ray Espinoza, Chief Information Security Officer, addressed the topic: Can you trust the public cloud? Is it ready for secure workloads?
Security and the Cloud – Common Myths:
Do you understand the real issues with security in the cloud and responsibilities
We’re extending his thoughts on some of the common myths about security in the cloud.
Myth #1: The cloud is inherently insecure
This myth stems from the natural perception that “anything outside my control is less secure.” And we don’t have to read much news today to realize that threats to business security are everywhere, and are mostly outside of our control.
But there are teams fighting every day to preserve personal and business security everywhere. Microsoft, for example, has developed an entire Digital Crimes Unit to make the Internet safer for consumers and businesses alike.
“When it comes to the cloud, trust and security are paramount,” noted Satya Nadella, Microsoft CEO.
The Digital Crimes Unit is a team of team of attorneys, investigators, forensic analysts and engineers. They use Microsoft Azure and Power BI to capture, store, and analyze over 600 million digital security threats every single day. They’re constantly monitoring and building security into the cloud itself.
And it’s working. Microsoft has just received the Pentagon’s highest cloud security rating – Information Impact Level 5 – for unclassified data.
At Atmosera, we put security at the center of everything we do. We focus our cloud solutions on Azure. We’ve developed an extensive suite of capabilities to improve your Information Security (InfoSec), including meeting rigorous compliance requirements for healthcare, financial services and government.
Our services include compliance for PCI-DSS, HIPAA/HITECH, HITRUST, and IRS-1075.
What can businesses do to ensure their security?
First, we recommend you develop a security strategy that supports your unique business needs. This requires working with a trusted advisor with the experience and knowledge to understand the gaps between where a company is, relative to information security, and best practices and security frameworks.
This broad gap assessment helps ensure all angles are carefully considered while identifying the potential risks and their implications for the organization. The next step is to create a Risk Registry which assists the organization catalog the known InfoSec risks. If the trusted advisor is not a cloud solution provider, their ability to support/offset some of your security needs and describe exactly which options they can provide will have to be understood. In the end, you need to have the confidence that you cloud solution provider has the people, technology and processes to keep your data and applications secure.
One of the first steps we take at Atmosera is to run an assessment – which includes a discovery around our customer’s unique security and compliance needs.
Myth #2: Security is the responsibility of the cloud solution provider
It turns out that security is a shared responsibility between a cloud solution provider and a company.
When you explore working with a cloud solution provider, such as Atmosera, you must be able to establish quickly:
- The role each party should play in securing your company’s data and applications
- The controls and workflows the cloud solution provider makes available to you
- And when to use them
You should expect the cloud solution provider to guide you on best practices and proactively help you establish a proper cloud and security strategy. You and your clouds solution provider are going to become partners – with shared responsibilities.
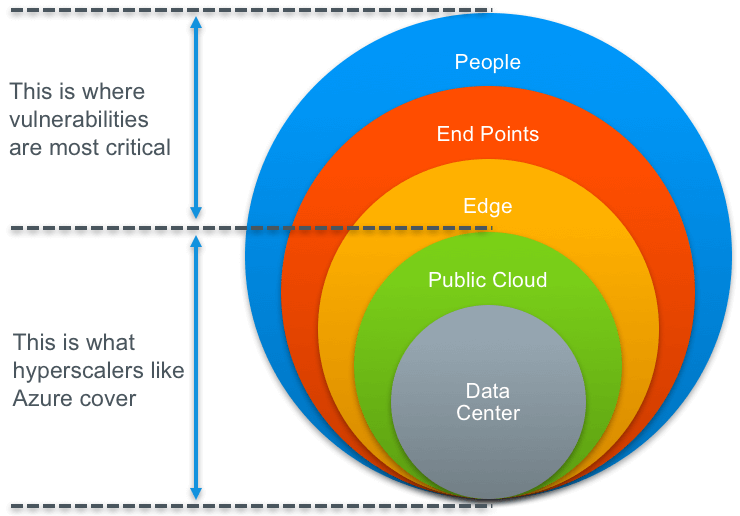
In terms of best practices, it’s critical to remember that security in the cloud is much more than protecting your data and your applications. You and your cloud solution provider must consider security implications end-to-end and especially mind the edges.
Companies must understand best practices around the people and processes surrounding access to their data and applications; but also those who can affect their data in motion, data at rest, and archiving data for the long-term.
It’s there that vulnerabilities are most critical and omnipresent, which is why (as Microsoft’s Satya says) security and trust are so essential.
Myth #3: The large public clouds provide all the security I need
Cloud hyperscalers, such as Microsoft Azure, have done an amazing job building massively scalable public clouds that reach all corners of the globe. They have made security a cornerstone and invest billions to keep your data and applications safe. However, they focus on the inner core which involves their data centers and the public facing clouds they power.
Trouble with the edge
The challenge goes beyond what the hyperscalers control. In fact, most vulnerabilities lie at the edge where people and the devices they use connect into the cloud. A proper security framework must be end-to-end and consider:
- The edge: which is predominantly the network including firewalls
- The endpoints: which include any devices used to access data and applications
- The people: how users are interacting with the data and how to restrict access
Create a plan
From a strategic perspective, you and your cloud solution provider must explore exactly which workloads you want to move into the cloud, and plan out how to protect them, end-to-end.
- How will you design and maintain information security best practices in a cloud environment?
- Do you need to meet specific compliance requirements i.e. HIPAA/HITECH, PCI-DSS or IRS-1075?
You’ll need to work with all of your vendors in developing a comprehensive information security (InfoSec) program. You’ll need to understand the capabilities and responsibilities that each of your vendors will take on as a part of a coordinated incident response program on your behalf, and you must have the cooperation of all of them to be able to test your plan. A competent cloud solution provider will help you with your InfoSec strategy and answer the following:
- How will you design and test your incident response plan?
- Where are vulnerabilities and how are they addressed?
- Who needs access to what data and applications?
- How will your monitor and react to possible intrusions or suspicious activities?
- How to identify a sustainable roadmap and remediate issues overtime?
- How can this environment keep up with my changing business needs?
Minding the edges may seem daunting, but can be made easier with the right trusted partner – and is essential as you consider the security of your most critical business assets.
Interested on exploring why Atmosera is trusted by hundreds of customers – as a cloud solution provider – around the globe?
We’d love to connect with you and talk through our Assessment process today.